
New Malware Alert: Noodlophile
The rise of AI tools has brought incredible innovation—but also a new breed of cyber threats. Meet Noodlophile, a newly discovered malware campaign riding the AI hype to trick users and steal sensitive data. This stealer malware isn’t just another cookie-cutter threat. It’s stealthy, well-crafted, and distributed through fake AI video platforms that look almost too good to be true. Spoiler alert: they are.
What is Noodlophile?
Noodlophile is an advanced piece of information-stealing malware. It’s being distributed as Malware-as-a-Service (MaaS) via dark web marketplaces, primarily targeting users interested in AI video generation tools.
Once installed, it steals:
- Browser credentials (usernames, passwords)
- Session cookies and authentication tokens
- Cryptocurrency wallet data
- Other personal info stored on your machine
How Does It Spread?
This campaign uses a classic social engineering bait-and-switch. Here’s the playbook:
- Fake AI Websites – Think names like “Dream Machine” that promise AI video creation.
- Social Media Ads – These fake tools are promoted in popular Facebook groups and forums.
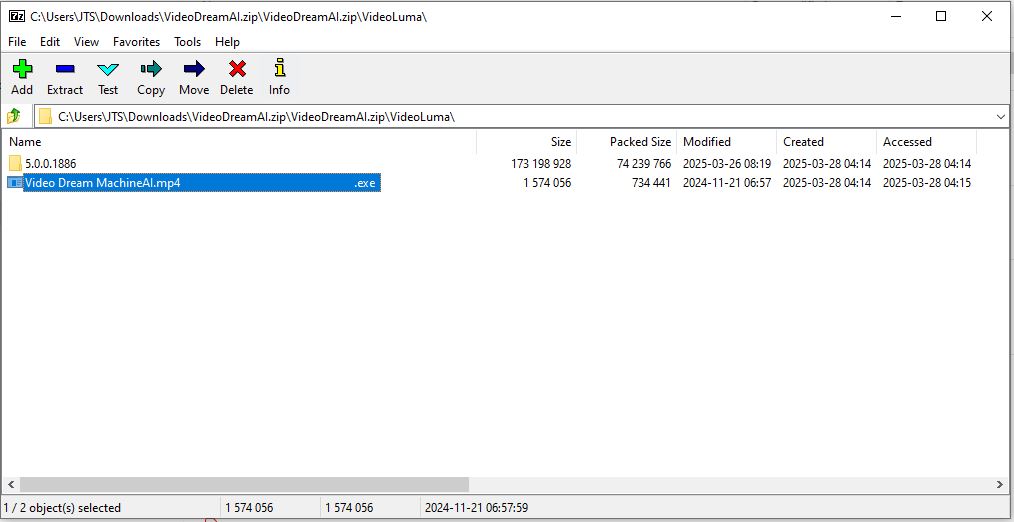
- Deceptive Download – Instead of a video, you get a ZIP file with malware disguised as a media player.
- Disguised Executables – The file (
Video Dream MachineAI.mp4.exe) looks like a video, but it’s an executable that kicks off the infection.
What Happens Behind the Scenes?
Once executed:
- The malware runs a batch script that:
- Uses
certutil.exeto unpack hidden files. - Adds itself to the Windows Registry for persistence.
- Downloads and runs a Python-based payload from a hardcoded server.
- Uses
- If Avast antivirus is detected, it uses PE hollowing. Otherwise, it uses shellcode injection.
- It sends stolen data in real time to a Telegram bot (command-and-control).
- Some variants come bundled with XWorm (a Remote Access Trojan).
Who’s Behind It?
Clues suggest the developer is Vietnamese-speaking and actively markets the malware in underground forums.
How to Stay Safe
To protect yourself and your organization:
- Be suspicious of free AI tools—especially those on social media.
- Check file extensions—watch out for disguised
.exefiles. - Enable file extension visibility in Windows Explorer.
- Use advanced endpoint protection with memory scanning.
- Don’t run unverified downloads.
Final Thoughts
Noodlophile is more than just malware—it’s a wake-up call. As AI excitement grows, so do the risks. If something seems too good (or futuristic) to be true, scan it before running it.
Have questions or insights? Leave a comment below or connect with us on LinkedIn/Twitter/YouTube!
